 |
Zebra 3 Report by Joe Anybody
Tuesday, 15 February 2011
COPWATCH in Atlanta - $40,000 dollaras and OK to fil the police
Mood:
 happy
Now Playing: Copwatchers sue city for taking camera phone - and win case in courts!
Topic: POLICE happy
Now Playing: Copwatchers sue city for taking camera phone - and win case in courts!
Topic: POLICE
http://m.ajc.com/news/atlanta/apd-wont-hinder-citizens-834521.html
Atlanta News
7:32 p.m. Thursday, February 10, 2011
APD won't hinder citizens who videotape cops
By Bill Rankin The Atlanta Journal-Constitution
Faced with complaints from a citizen watchdog group, Atlanta police
will stop interfering with people who videotape officers performing
their duties in public, an agreement reached with the city Thursday
says.
The settlement, which also calls for the city to pay $40,000 in
damages, requires city council approval.
The agreement resolves a complaint filed by Marlon Kautz and Copwatch
of East Atlanta, a group that films police activity with cell phones
and hand-held cameras. The group has volunteers who go out on patrols
and begin videotaping police activity when they come across it.
Last April, Kautz said, he pulled out his camera phone and began
recording Atlanta police who were arresting a suspect in Little Five
Points. Two officers approached him and said he had no right to be
filming them, Kautz said. When Kautz refused to stop, one officer
wrenched Kautz's arm behind his back and yanked the camera out of his
hands, he said.
"I was definitely scared," Kautz, 27, said.
Kautz said that when he asked to get his phone back, another officer
said he'd return it only after Kautz gave him the password to the
phone so he could delete the footage. When Kautz refused, police
confiscated the phone, he said. When police returned it, Kautz said,
the video images had been deleted, altered or damaged.
As part of Thursday's settlement, reached before a civil rights
lawsuit was filed, the city will pay Kautz and Copwatch of East
Atlanta $40,000 in damages. APD will also adopt an operating procedure
that prohibits officers from interfering with citizens who are taping
police activity, provided individuals recording the activity do not
physically interfere with what the officers are doing. The policy is
to be adopted within 30 days after the Atlanta city council approves
the settlement, and training is to be carried out during police roll
calls.
"We commend the city for resolving a long-standing problem of police
interfering with citizens who monitor police activity," the group's
lawyers, Gerry Weber and Dan Grossman, said.
APD spokesman Carlos Campos said the matter had been referred to the
Office of Professional Standards, and three officers were disciplined.
The two officers who confronted Kautz -- Mark Taylor and Anthony
Kirkman -- received oral admonishments for failing to take appropriate
action. Sgt. Stephen Zygai was admonished for failure to supervise.
"Commanders have made it clear that Atlanta police officers in the
field should not interfere with a citizen's right to film them while
they work in public areas," Campos said.
Also Thursday, the Atlanta Citizen Review Board sustained allegations
of excessive force against Kirkman, who took the phone out of Kautz's
hand. The board recommended to Police Chief George Turner that Kirkman
be suspended without pay for four days. It also recommended that APD
adopt the new standard operating procedure.
Copwatch began in 1990 in Berkeley, Calif., and other chapters have
since been organized in cities across the country. Its goal is to
protect citizens from being mistreated by holding police accountable.
With the ubiquity of small hand-held cameras and cell phones, Copwatch
members can begin videotaping a police scene at a moment's notice.
"There shouldn't be anything wrong with these constitutional watchdogs
keeping an eye on the police," said Emory University law professor Kay
Levine. "Just about anything the police are doing out in the public,
in performance of their duties, members of the public can see -- and
therefore film."
Citizens should not interfere with police activity, however, and
should be wary about compromising an undercover investigation, she
said.
"Just about anything the police are doing out in the public, they
should be comfortable being videotaped because they're simply
performing their duties," Levine said. "If some aren't comfortable
with it, it makes you wonder why."
Kautz started Copwatch of East Atlanta after he moved here about two
years ago.
"We landed right smack dab in a situation where we saw police behavior
was unacceptable," Kautz said, citing the controversial APD raid of
the Atlanta Eagle gay bar. "We saw Copwatch as direct action we could
take to increase police accountability in the city."
Copwatch members are trained how to behave when videotaping a scene,
Kautz said. "It's important for us when we're out there to keep it
together. We try to stay professional, as we expect the police to be."
Copwatch members get varying responses from police, Vincent
Castillenti, 24, said. Some officers become hostile because they don't
like the scrutiny, while others begin behaving less aggressively when
they realize they're being filmed, he said.
Kautz said the intent of Copwatch is not to get police officers in
trouble. "The hope," he said, "is that our presence will remind police
the community is watching what they're doing and wants them to be on
their best behavior."
Posted by Joe Anybody
at 10:45 AM PST
Monday, 14 February 2011
What did he say?
Mood:
 mischievious
Now Playing: click the link
Topic: SMILE SMILE SMILE mischievious
Now Playing: click the link
Topic: SMILE SMILE SMILE
Hello ! 
click --> Dialtone
Posted by Joe Anybody
at 12:50 PM PST
Updated: Monday, 14 February 2011 12:55 PM PST
Wednesday, 9 February 2011
No Internet due to the nGovernment "shutting it down" - Suggestion are here
Mood:
 lucky
Now Playing: How to Communicate if the Government Shut Down the Internet
Topic: MEDIA lucky
Now Playing: How to Communicate if the Government Shut Down the Internet
Topic: MEDIA
February 9th, 2011 http://dprogram.net/2011/02/09/how-to-communicate-if-the-government-shut-down-the-internet/?utm_source=twitterfeed&utm_medium=twitter
(LibertyNewsOnline) – Scenario: Your government is displeased with the communication going on in your location and pulls the plug on your internet access, most likely by telling the major ISPs to turn off service.  This is what happened in Egypt Jan. 25 prompted by citizen protests, with sources estimating that the Egyptian government cut off approximately 88 percent of the country’s internet access. What do you do without internet? Step 1: Stop crying in the corner. Then start taking steps to reconnect with your network. Here’s a list of things you can do to keep the communication flowing. This is what happened in Egypt Jan. 25 prompted by citizen protests, with sources estimating that the Egyptian government cut off approximately 88 percent of the country’s internet access. What do you do without internet? Step 1: Stop crying in the corner. Then start taking steps to reconnect with your network. Here’s a list of things you can do to keep the communication flowing.
NOTE: If you have advice to add, please log in and Aadd your comments. ——————— PREVENTIVE MEASURES: MAKE YOUR NETWORK TANGIBLE Print out your contact list, so your phone numbers aren’t stuck in the cloud. Some mail services like Gmail allow you to export your online contact list in formats that are more conducive to paper, such as CSV or Vcard, and offer step-by-step guides on how to do this. BROADCAST ON THE RADIO: CB Radio: Short for “Citizens Band” radio, these two-way radios allow communication over short distances on 40 channels. You can pick one up for about $20 to $50 at Radio Shack, and no license is required to operate it. Ham radio: To converse over these radios, also known as “amateur radios,” you have to obtain an operator’s license from the FCC. Luckily, other Wired How-To contributors have already explained exactly what you need to do to get one and use it like a pro. However, if the President declares a State of Emergency, use of the radio could be extremely restricted or prohibited. GMRS: The General Mobile Radio Service (GMRS) is a licensed land-mobile FM UHF radio service in the United States available for short-distance two-way communication. It is intended for use by an adult individual who possesses a valid GMRS license, as well as his or her immediate family members… They are more expensive than the walkie talkies typically found in discount electronics stores, but are higher quality. Family Radio Service: The Family Radio Service (FRS) is an improved walkie talkie radio system authorized in the United States since 1996. This personal radio service uses channelized frequencies in the ultra high frequency (UHF) band. It does not suffer the interference effects found on citizens’ band (CB) at 27 MHz, or the 49 MHz band also used by cordless phones, toys, and baby monitors. Microbroadcasting: Microbroadcasting is the process of broadcasting a message to a relatively small audience. This is not to be confused with low-power broadcasting. In radio terms, it is the use of low-power transmitters to broadcast a radio signal over the space of a neighborhood or small town. Similarly to pirate radio, microbroadcasters generally operate without a license from the local regulation body, but sacrifice range in favor of using legal power limits. Packet Radio Back to the ’90s: There do exist shortwave packet-radio modems. These are also excruciatingly slow, but may get your e-mail out. Like ham radio above it requires a ham radio license because they operate on ham radio frequencies. TELEPHONE: Set up a phone tree: According to the American Association of University Women, a phone tree is “a prearranged, pyramid-shaped system for activating a group of people by telephone” that can “spread a brief message quickly and efficiently to a large number of people.” Dig out that contact list you printed out to spread the message down your pyramid of contacts. Enable Twitter via SMS: Though the thought of unleashing the Twitter fire hose in your text message inbox may seem horrifying, it would be better than not being able to connect to the outside world at all. The Twitter website has full instructions on how to redirect tweets to your phone. Call to Tweet: A small team of engineers from Twitter, Google and SayNow, a company Google acquired recently, made this idea a reality. It’s already live and anyone can tweet by simply leaving a voicemail on one of these international phone numbers (+16504194196 or +390662207294 or +97316199855) and the service will instantly tweet the message using the hashtag #egypt. No Internet connection is required. People can listen to the messages by dialing the same phone numbers or going to the Twitter account, speak2tweet. Alex Jones and infowars.com have a telephone number for people to listen to his radio show by phone, in case the internet goes down, or if you don’t have internet. The phone in listen line is 512-646-5000. FAX: If you need to quickly send and receive documents with lengthy or complex instructions, phone conversations may result in misunderstandings, and delivering the doc by foot would take forever. Brush the dust off that bulky old machine, establish a connection by phone first with the recipient to make sure his machine is hooked up, then fax away. You may not need a fax machine to send or receive faxes if your computer has a dial-up fax application. NON-VIRTUAL BULLETIN BOARD Sometimes we get so wrapped up in the virtual world that we forget about resources available in the real world. Physical bulletin boards have been used for centuries to disseminate information and don’t require electricity to function. If you are fortunate enough to be getting information from some other source why not share it with your friends and neighbors with your own bulletin board? Cork, magnetic and marker bulletin boards are as close as your nearest dime store and can be mounted just about anywhere. And if push comes to shove you can easily make your own with scrap wood lying around the house. Getting back onlineWhile it might be relatively easy for a government to cut connections by leveraging the major ISPs, there are some places they wouldn’t get to so readily, like privately-owned networks and independent ISPs. FIND THE PRIVATELY RUN ISPs In densely populated areas, especially in central business districts and city suburbs there are multiple home WiFi networks overlapping each other, some secure, some not. If there is no internet, open up your WiFi by removing password protection: If enough people do this it’s feasible to create a totally private WiFi service outside government control covering the CBD, and you can use applications that run Bonjour (iChat on Mac for example) to communicate with others on the open network and send and receive documents. **needs more clarification If you are a private ISP, it’s your time to shine. Consider allowing open access to your Wi-Fi routers to facilitate communication of people around you until the grid is back online. RETURN TO DIAL-UP According to an article in the BBC about old tech’s role in the Egyptian protests, “Dial-up modems are one of the most popular routes for Egyptians to get back online. Long lists of international numbers that connect to dial-up modems are circulating in Egypt thanks to net activists We Re-Build, Telecomix and others.” Dial-up can be slow. Often, there is a lightweight mobile version of a site that you can load from your desktop browser quickly despite the limitations of dial-up. Examples: mobile.twitter.com, m.facebook.com, m.gmail.com.
AD-HOC NETWORKING Most wireless routers, PCs, laptops, and even some ultramobile devices like cellphones have the ability to become part of an “ad hoc” network, where different “nodes” (all of the devices on the network) share the responsibility of transmitting data with one another. These networks can become quite large, and are often very easy to set up. If used properly by a tech-savvy person, such networks can be used to host temporary websites and chat rooms. There are many internet tutorials on the internet for ad hoc networking, so feel free to google some. Apple computers tend to have very accessible ad hoc functionality built in, including a pre-installed chat client (iChat) that will automatically set up an ad hoc “Rendezvous” chatroom among anybody on the network, without the need for an external service like AIM or Skype. Ad hoc network-hosting functionality is built in to the Wi-Fi menu. Windows computers have several third-party ad hoc chat applications available (such as Trillian) and setting up an ad hoc Wi-Fi network is almost as simple as on a Mac. Linux operating systems, of course, have plenty of third-party apps available, and most distros have ad hoc network-creation support built in. BUILD LARGE BRIDGED WIRELESS NETWORK Using popular wireless access point devices like a Linksys WRT54G, you can create a huge wireless bridged network — effectively creating a Local Area Network (LAN), or a private Internet that can be utilized by all users within range using a Wi-Fi enabled device. You can also link multiple devices together wirelessly, extending the range of your network. Most access points will cover a 100 meter area and if your wireless device is built to support the 802.11n wireless standard, you will get almost a 500 meter coverage area for each access point. To build a wireless bridge, check out the dd-wrt wiki, and learn how to configure Linksys WRT54G as a wireless client using this Anandtech thread. NINTENDO DS A used DS family device can be purchased inexpensively. In addition to wi-fi, the DS supports its own wireless protocols. Using Pictochat, it is possible to chat with nearby DS users without having any DS games. Unfortunately, the range is quite short. Some games, such as the fourth generation Pokemon games, support mail items. Thus you can send your message under the guise of just playing a game. Mail items can be sent through the Internet if you can get on the net and you and your partner(s) have each other’s friend codes. The original DS and the DS Lite do support the Opera web browser, but finding the game card and memory pack may be very difficult. Starting with the DSi, Opera is downloadable. INTRANET Your computer has the ability to set up your own INTRANET. This was done BEFORE the internet was popularized in two ways: Your computer dialed up other computers and sent them the contents of a message board, or local people people dialed into your computer. A nationwide system can be set up this way with a central location sending to many cities then each city sending out the info locally. BECOME UNTRACEABLE If you’re going to post government secrets on your work-around site, you may want to set up an untraceable account. Really, you only need a mail drop, an assumed name, a prepaid credit card you can get at many stores to set up service. GET SATELLITE ACCESS You can have very, very slow internet if you have something similiar to an Iridium phone, which would allow you to do dial up at 2400 baud, which at least gives you e-mail. This will also work when your government has shut down GSM and telephone access, and will work pretty much anywhere on the planet. If you’re in the right place, get yourself KA-SAT access which is satellite broadband and will not be routed through any internet exchange that certain local governments may monitor or block (unless that government is part of EU or er … Uncle Sam. BACK TO BASICS Make some noise: Have an air horn or other loud instrument handy. It may just come down to being able to alert people in your local geographic area, who would otherwise be unaware of an emergency. You may also want to learn a bit about Morse code and have a cheat sheet available.
Posted by Joe Anybody
at 11:45 AM PST
Tuesday, 8 February 2011
FBI want to join with Portland Police - Listen about FBI spying on Antiwar-Peace groups
Mood:
 incredulous
Now Playing: Tom Burghardt expains how FBI
Topic: FAILURE by the GOVERNMENT incredulous
Now Playing: Tom Burghardt expains how FBI
Topic: FAILURE by the GOVERNMENT
http://portland.indymedia.org/en/2011/02/405926.shtml
American Police State: FBI Abuses Reveals Contempt for Political Rights, Civil Liberties  A As mass revolt spreads across Egypt and the Middle East and citizens there demand jobs, civil liberties and an end to police state abuses from repressive, U.S.-backed torture regimes, the Obama administration and their congressional allies aim to expand one right here at home. Last week, the Electronic Frontier Foundation ( EFF) released an explosive new report documenting the lawless, constitutional-free zone under construction in America for nearly a decade. That report, "Patterns of Misconduct: FBI Intelligence Violations from 2001-2008," reveals that the domestic political intelligence apparat spearheaded by the Federal Bureau of Investigation, continues to systematically violate the rights of American citizens and legal residents. A rather ironic state of affairs considering the free passes handed out by U.S. securocrats to actual terrorists who killed thousands of Americans on 9/11, as both WikiLeaks and FBI whistleblower Sibel Edmonds disclosed last week. Although illegal practices and violations were reported by the FBI to the Intelligence Oversight Board (IOB) after an unexplained two-and-a-half-year delay, a further violation of lawful guidelines, lawbreaking continued unabated; in fact, it accelerated as the Bureau was given a green light to do so by successive U.S. administrations. The IOB is a largely toothless body created in 1976 by the Ford administration in the wake of disclosures of widespread spying and infiltration of political groups by America's secret state agencies during the sixties and seventies. Reeling from revelations uncovered by Congress, investigative journalists and citizen activists in the wake of the Watergate scandal, Ford's caretaker government was forced to call a halt to the more egregious practices employed by the FBI to keep the lid on and crafted guidelines governing intelligence and surveillance operations. In fact, the Attorney General's Guidelines regulating both FBI National Security Investigations and Foreign Intelligence Collection ( NSIG) stipulate that "all government intelligence operations occur with sufficient oversight and within the bounds of the Constitution and other federal laws." While it can rightly be argued these protocols were largely ineffective, and had been breeched more often than not by the 1980s under President Reagan, as revealed during the Iran-Contra scandal, and that antiwar, environmental and solidarity groups continue to be spied upon and destabilized by agents provocateurs and right-wing corporate scum, they were thrown overboard entirely by the Bush regime in the aftermath of the 9/11 attacks. Today the "looking forward, not backward" Obama administration has whole-heartedly embraced Bushist lawlessness while charting an even more sinister course of their own, now asserting they have the authority to assassinate American citizens the Executive Branch designate as "terrorists" anywhere on earth without benefit of due process or court review. According to EFF, more than 2,500 documents obtained under the Freedom of Information Act revealed that: * From 2001 to 2008, the FBI reported to the IOB approximately 800 violations of laws, Executive Orders, or other regulations governing intelligence investigations, although this number likely significantly under-represents the number of violations that actually occurred.
* From 2001 to 2008, the FBI investigated, at minimum, 7000 potential violations of laws, Executive Orders, or other regulations governing intelligence investigations.
* Based on the proportion of violations reported to the IOB and the FBI's own statements regarding the number of NSL [National Security Letter] violations that occurred, the actual number of violations that may have occurred from 2001 to 2008 could approach 40,000 possible violations of law, Executive Order, or other regulations governing intelligence investigations. (Electronic Frontier Foundation, Patterns of Misconduct: FBI Intelligence Violations from 2001-2008, January 30, 2011) But FBI lawbreaking didn't stop there. Citing internal documents, EFF revealed that the Bureau also "engaged in a number of flagrant legal violations" that included, "submitting false or inaccurate declarations to courts," "using improper evidence to obtain federal grand jury subpoenas" and "accessing password protected documents without a warrant." In other words, in order to illegally spy on Americans and haul political dissidents before Star Chamber-style grand juries, the FBI routinely committed perjury and did so with absolute impunity. Reviewing the more than 2,500 documents EFF analysts averred that they had "uncovered alarming trends in the Bureau's intelligence investigation practices" and that the "documents suggest the FBI's intelligence investigations have compromised the civil liberties of American citizens far more frequently, and to a greater extent, than was previously assumed." According to EFF, the "documents show that the FBI most frequently committed three types of intelligence violations--violations of internal oversight guidelines for conducting investigations; violations stemming from the abuse of National Security Letters; and violations of the Fourth Amendment, Foreign Intelligence Surveillance Act (FISA), and other laws governing intelligence investigations." "Based on statements made by government officials and the proportion of violations occurring in the released reports," EFF estimates that "the FBI may have committed as many as 40,000 intelligence investigation violations over the past ten years." The civil liberties' watchdogs revealed that the type of violation occurring most frequently involved the Bureau's abuse of National Security Letters (NSLs), onerous lettres de cachet, secretive administrative subpoenas with built-in gag orders used by the FBI to seize records from third-parties without any judicial review whatsoever. Although National Security Letters have been employed by investigators since the 1970s, after 9/11 Congress passed the repressive USA PATRIOT Act which "greatly expanded the intelligence community's authority to issue NSLs." "During the course of a terrorism or counterintelligence investigation," EFF writes, "NSLs can be used to obtain just three types of records: (1) subscriber and 'toll billing information' from telephone companies and 'electronic communications services;' (2) financial records from banks and other financial institutions; and (3) consumer identifying information and the identity of financial institutions from credit bureaus." Abuses have been well-documented by the Justice Department's own Office of the Inspector General. In their 2008 report, the OIG disclosed that the FBI issued some 200,000 requests and that almost 60% were for investigations of U.S. citizens and legal residents. Given the symbiosis amongst American secret state agencies and grifting corporations, EFF discovered that "the frequency with which companies [received] NSLs--phone companies, internet providers, banks, or credit bureaus--contributed to the FBI’s NSL abuse." "In over half of all NSL violations reviewed by EFF, the private entity receiving the NSL either provided more information than requested or turned over information without receiving a valid legal justification from the FBI." In fact, "companies were all too willing to comply with the FBI's requests, and--in many cases--the Bureau readily incorporated the over-produced information into its investigatory databases." This too is hardly surprising, given the enormous profits generated by the surveillance state for their corporate beneficiaries. As The Washington Post revealed in their investigative series, Top Secret America, more than 800,000 corporate employees have been issued top secret and above security clearances. Beholden to their employers and not the public who foots the bill and is the victim of their excesses, accountability is a fiction and oversight a contemptible fraud. In a follow-up piece, Monitoring America, investigative journalists Dana Priest and William M. Arkin revealed that the FBI "is building a database with the names and certain personal information, such as employment history, of thousands of U.S. citizens and residents whom a local police officer or a fellow citizen believed to be acting suspiciously." In other words, in order to "keep us safe" unaccountable securocrats are constructing a Stasi-like political intelligence system that has overthrown the traditional legal concept of probable cause in favor of a regime rooted in fear and suspicion; one where innocent activities such as taking a photograph or attending an antiwar rally now serves as a pretext for opening a national security investigation. According to Priest and Arkin, the Bureau database "is accessible to an increasing number of local law enforcement and military criminal investigators, increasing concerns that it could somehow end up in the public domain," and used by employers to terminate political dissidents or other "undesirable" citizens merely on the basis of allegations emanating from who knows where. As Antifascist Calling reported in October, "predictive behavior" security firms, generously funded by the CIA's venture capitalist arm, In-Q-Tel, have increasingly turned to monitoring social media sites such as Blogger, Facebook, Flickr, Twitter and YouTube and are exploiting powerful computer algorithms for their clients--your boss--thereby transforming private communications into "actionable intelligence" that just might get you fired. In one case, EFF discovered that the FBI "requested email header information for two email addresses used by a U.S. person." In response, researchers averred "the email service provider returned two CDs containing the full content of all emails in the accounts. The FBI eventually (and properly) sequestered the CDs, notified the email provider of the overproduction, and re-issued an NSL for the originally requested header information; but, in response to the second NSL, the email provider again provided the FBI with the full content of all emails in the accounts." To make matters worse, "third-parties not only willingly cooperated with FBI NSLs when the legal justification was unclear, however: they responded to NSLs without any legal justification at all." In conclusion, EFF wrote that "while the reports documenting the FBI's abuse of the Constitution, FISA, and other intelligence laws are troubling, EFF's analysis is necessarily incomplete: it is impossible to know the severity of the FBI's legal violations until the Bureau stops concealing its most serious violations behind a wall of arbitrary secrecy." This sordid state of affairs is likely to continue given Congress's utter lack of interest in protecting Americans' constitutionally-protected right to privacy, free speech and assembly. With new moves afoot in Congress to pass a data retention law that requires internet service providers to retain records of users' online activity or, as in the repressive Egyptian U.S. client state, handing the Executive Branch a "kill-switch" that would disconnect the American people from the internet in the event of a "national emergency," the U.S. oligarchy is planning for the future. As the World Socialist Web Site points out, "The US government is well aware that the Internet provides a forum for rapid communication and organization, as demonstrated by the events in Egypt this week. In an attempt to block communication within Egypt and with the external world, US-backed dictator Hosni Mubarak cut off the country's access to the Internet altogether." "Similarly," left-wing journalist Patrick Zimmerman writes, "the fundamental goal of the US government in its attempts to gain control of the Internet and monitor user activity has nothing to do with the 'war on terror' or prosecuting criminals. Under conditions of growing social inequality, government austerity, and expanding war abroad, the government anticipates the growth of social opposition in the United States." The Bush regime's "preemptive war" doctrine has been fully incorporated into the Obama administration's "homeland security" paradigm. The formidable police state apparatus that accompanies America's imperial adventures abroad are now deployed at home where they have devastating effects on an already dysfunctional democracy sliding ever-closer towards an authoritarian abyss. Tom Burghardt is a researcher and activist based in the San Francisco Bay Area. In addition to publishing in Covert Action Quarterly and Global Research, an independent research and media group of writers, scholars, journalists and activists based in Montreal, his articles can be read onDissident Voice, The Intelligence Daily, Pacific Free Press, Uncommon Thought Journal, and the whistleblowing website WikiLeaks. He is the editor of Police State America: U.S. Military "Civil Disturbance" Planning, distributed by AK Press and has contributed to the new book from Global Research, The Global Economic Crisis: The Great Depression of the XXI Century. |
Posted by Joe Anybody
at 9:14 PM PST
Monday, 7 February 2011
Portland Indymedia Principles of Unity
Mood:
 lyrical
Now Playing: UNITY AND - YOU BE THE MEDIA ((( i )))
Topic: MEDIA lyrical
Now Playing: UNITY AND - YOU BE THE MEDIA ((( i )))
Topic: MEDIA
Portland Indymedia Principles of Unity
 - All portland indymedia working groups are not-for-profit. All volunteers donate their time and have agreed to receive no personal monetary gain. In otherwords, nobody gets paid.
- All working groups recognize the importance of process to social change and are committed to the development of non-hierarchical and anti-authoritarian relationships, from interpersonal relationships to group dynamics. Therefore, they shall organize themselves collectively and be committed to the principle of consensus decision-making and the development of a direct, participatory democratic process that is transparent to those involved.
- All working groups recognize that the contribution of an individual's labor is a prerequisite for participation in the decision making process of a working group or at a portland indymedia general meeting. Individuals who are not committing tangible labor to a portland indymedia working group are encouraged to share their views but may not "block" a consensus.
- All working groups are committed to caring for one another and their respective communities both collectively and as individuals and will promote the sharing of resources including knowledge, skills and equipment.
- Whenever possible, all working groups shall be committed to the use of free software and open source code, in order to develop the digital infrastructure, and to increase the independence of themselves by not relying on proprietary software.
- Openess: All working groups shall be committed to the principle of human equality, and shall not discriminate based upon race, spiritual belief, gender, age, class or sexual identity. Working groups are committed to the ideal of building diversity within their activities.
============================================================== PRINCIPLES OF UNITY 1. The Independent Media Center Network (IMCN) is based upon principles of equality, decentralization and local autonomy. The IMCN is not derived from a centralized bureaucratic process, but from the self-organization of autonomous collectives that recognize the importance in developing a union of networks. 2. All IMC's consider open exchange of and open access to information a prerequisite to the building of a more free and just society. [3. All IMC's respect the right of activists who choose not to be photographed or filmed.] 4. All IMC's, based upon the trust of their contributors and readers, shall utilize open web based publishing, allowing individuals, groups and organizations to express their views, anonymously if desired. **see appendix: Open Publishing document --> still in proposal phase, at this address: http://lists.indymedia.org/mailman/public/imc-communication/2001-April/001707.html http://lists.indymedia.org/mailman/public/imc-communication/2001-April/000874.html 5. The IMC Network and all local IMC collectives shall be not-for-profit. 6. All IMC's recognize the importance of process to social change and are committed to the development of non-hierarchical and anti-authoritarian relationships, from interpersonal relationships to group dynamics. Therefore, shall organize themselves collectively and be committed to the principle of consensus decision making and the development of a direct, participatory democratic process] that is transparent to its membership. 7. [All IMC's recognize that a prerequisite for participation in the decision making process of each local group is the contribution of an individual's labor to the group.] 8. All IMC's are committed to caring for one another and our respective communities both collectively and as individuals and will promote the sharing of resources including knowledge, skills and equipment. 9. All IMC's shall be committed to the use of free source code, whenever possible, in order to develop the digital infrastructure, and to increase the independence of the network by not relying on proprietary software. 10. All IMC's shall be committed to the principle of human equality, and shall not discriminate, including discrimination based upon race, gender, age, class or sexual orientation. Recognizing the vast cultural traditions within the network, we are committed to building [diversity] within our localities.
Posted by Joe Anybody
at 12:04 PM PST
Sunday, 6 February 2011
A defense mechanism, which they labeled “backfire...
Mood:
 d'oh
Now Playing: Stephen Dufrechou - Are We Too Dumb for Democracy?
Topic: CONSPIRACY d'oh
Now Playing: Stephen Dufrechou - Are We Too Dumb for Democracy?
Topic: CONSPIRACY
Stephen Dufrechou - Are We Too Dumb for Democracy? The Logic Behind Self-Delusion
That's not a rhetorical question. But I also am not convinced "dumb" is the right word. Dufrechou is solid footing in referencing George Lakoff, but much less so when referring to psychoanalysis.
To be honest, Dufrechou has it backwards in saying that psychoanalysis supports Lakoff's research - it's the other way around. There is little to no empirical support for psychoanalysis, while Lakoff, as a linguist, is rivaled only by Chomsky.
Anyway, this is an interesting look at why people hold on to false beliefs in the face of overwhelming evidence to the contrary.
When faced with facts that do not fit seamlessly into our individual belief systems, our minds automatically reject (or backfire) the presented facts.
Stephen Dufrechou | December 19, 2010
A recent cognitive study, as reported by the Boston Globe, concluded that: Facts don’t necessarily have the power to change our minds. In fact, quite the opposite. In a series of studies in 2005 and 2006, researchers at the University of Michigan found that when misinformed people, particularly political partisans, were exposed to corrected facts in news stories, they rarely changed their minds. In fact, they often became even more strongly set in their beliefs. Facts, they found, were not curing misinformation. Like an underpowered antibiotic, facts could actually make misinformation even stronger.
In light of these findings, researchers concluded that a defense mechanism, which they labeled “backfire”, was preventing individuals from producing pure rational thought. The result is a self-delusion that appears so regularly in normal thinking that we fail to detect it in ourselves, and often in others: When faced with facts that do not fit seamlessly into our individual belief systems, our minds automatically reject (or backfire) the presented facts. The result of backfire is that we become even more entrenched in our beliefs, even if those beliefs are totally or partially false. “The general idea is that it’s absolutely threatening to admit you’re wrong,” said Brendan Nyhan, the lead researcher of the Michigan study. The occurrence of backfire, he noted, is “a natural defense mechanism to avoid that cognitive dissonance.” The conclusion made here is this: facts often do not determine our beliefs, but rather our beliefs (usually non-rational beliefs) determine the facts that we accept. As the Boston Globe article notes: In reality, we often base our opinions on our beliefs, which can have an uneasy relationship with facts. And rather than facts driving beliefs, our beliefs can dictate the facts we chose to accept. They can cause us to twist facts so they fit better with our preconceived notions. Worst of all, they can lead us to uncritically accept bad information just because it reinforces our beliefs. This reinforcement makes us more confident we’re right, and even less likely to listen to any new information. And then we vote.
Despite this finding, Nyhan claims that the underlying cause of backfire is unclear. “It’s very much up in the air,” he says. And on how our society is going to counter this phenomena, Nyhan is even less certain. These latter unanswered questions are expected in any field of research, since every field has its own limitations. Yet here the field of psychoanalysis can offer a completion of the picture. Disavowal and Backfire: One and the Same In an article by psychoanalyst Rex Butler, Butler independently comes to the same conclusion as the Michigan Study researchers. In regards to facts and their relationship to belief systems (or ideologies), Butler says that: there is no necessary relationship between reality and its symbolization … Our descriptions do not naturally and immutably refer to things, but … things in retrospect begin to resemble their description. Thus, in the analysis of ideology, it is not simply a matter of seeing which account of reality best matches the ‘facts’, with the one that is closest being the least biased and therefore the best. As soon as the facts are determined, we have already – whether we know it or not – made our choice; we are already within one ideological system or another. The real dispute has already taken place over what is to count as the facts, which facts are relevant, and so on.
This places the field of psychoanalysis on the same footing as that of cognitive science, in regards to this matter. But where cognitive studies end, with Nyhan’s question about the cause of backfire, psychoanalysis picks up and provides a possible answer. In fact, psychoanalysts have been publishing work on backfire for decades; only psychoanalysis refers to backfire by another name: “disavowal”. Indeed, these two terms refer to one and the same phenomena. The basic explanation for the underlying cause of disavowal/backfire goes as follows. “Liberals” and “conservatives” espouse antithetical belief systems, both of which are based on different non-rational “moral values.” This is a fact that cognitive linguist George Lakoff has often discussed, which incidentally brings in yet another field of study that supports the existence of the disavowal/backfire mechanism. In accordance with these different non-rational belief systems, any individual’s ideology tends to function also as a ‘filtering system’, accepting facts that seamlessly fit into the framework of that ideology, while dismissing facts that do not fit. When an individual—whether a “liberal”, “conservative”, or any other potential ideology—is challenged with facts that conflict with his/her ideology, the tendency is for that individual to experience feelings of anxiety, dread, and frustration. This is because our ideologies function, like a lynch pin, to hold our psychologies together, in order to avoid, as Nyhan puts it, “cognitive dissonance”. In other words, when our lynch pins are disturbed, our psychologies are shaken. Psychoanalysts explain that, when this cognitive dissonance does occur, the result is to ‘externalize’ the sudden negative feelings outward, in the form of anger or resentment, and then to ‘project’ this anger onto the person that initially presented the set of backfired facts to begin with. (Although, sometimes this anger is ‘introjected’ inward, in the form of self-punishment or self-loathing.) This non-rational eruption of anger or resentment is what psychoanalysts call “de-sublimation”. And it is at the point of de-sublimation, when the disavowal/backfire mechanism is triggered as a defense against the cognitive dissonance. Hence, here is what mentally occurs next, in a matter of seconds: In order to regain psychological equilibrium, the mind disavows the toxic facts that initially clashed with the individuals own ideology, non-rationally deeming the facts to be false—without assessing the validity of the facts. The final step occurs when the person, who offered the toxic facts, is then non-rationally demonized. The person, here, becomes tainted as a ‘phobic object’ in the mind of the de-sublimated individual. Hence, the other person also becomes perceived to be as toxic as the disavowed facts, themselves. At this point, ad hominem attacks are often fired at the source of the toxic facts. For example: ‘stupid liberal’ or ‘stupid conservative’, if in a political context. Or, ‘blasphemer’ or ‘heretic’, if in a religious context. At this point, according to psychoanalysis, psychological equilibrium is regained. The status quo of the individual’s ideology is reinforced to guard against future experiences of de-sublimation. Why Do Different Ideologies Exist? This all begs the obvious question about the existence of differing ideologies between people. Why do they exist? And how are they constituted differently? George Lakoff has demonstrated in his studies (which are supported strongly by psychoanalysis), that human beings are not born already believing an ideology. Rather people are socialized into an ideology during their childhood formative years. The main agents which prescribe the ideology are the parental authority figures surrounding the child, who rear him, from infantile dependency on the parent-figures, into an independent adult. The parental values of how the child should be an independent and responsible adult, in regards to his relations between his self and others, later informs that child’s ideology as an adult. Lakoff shows that two dominant parenting types exist, which can determine the child’s adult ideology. Individuals reared under the “Strict Parent” model tend to grow-up as political conservatives, while those raised under a “Nurturing Parent” model tend to become political liberals. His most influential book on these matters, “Moral Politics: How Liberals and Conservatives Think”, was published in 1996. Of course, peoples’ minds can fundamentally change, along with their ideological values. But short of a concerted effort by an individual to change, through one form of therapy or another, that change is mostly fostered by traumatic or long-endured life experiences. Yet many minds remain rock solid for life, beliefs included. As psychiatrist Scott Peck sees it, “Only a relative and fortunate few continue until the moment of death exploring the mystery of reality, ever enlarging and refining and redefining their understanding of the world and what is true.” Thus to answer Nyahan’s question—how can society counter the negative effects of backfire?—it seems only one answer is viable. Society will need to adopt the truths uncovered by cognitive science and psychoanalysis. And society will have to use those truths to inform their overall cultural practices and values. Short of that, Peck’s “fortunate few” will remain the only individuals among us who resist self-delusion. ~ Stephen Dufrechou is Editor of Opinion and Analysis for News Junkie Post.
Posted by Joe Anybody
at 12:01 AM PST
Updated: Monday, 7 February 2011 9:55 AM PST
Saturday, 5 February 2011
TWEET - Hear Me - ... Oh I do!... ReTweet Tweet tweet
Mood:
 happy
Now Playing: Social Media & Why one person usees Twitter
Topic: MEDIA happy
Now Playing: Social Media & Why one person usees Twitter
Topic: MEDIA
Posted on | February 5, 2011 | http://www.inkstain.net/fleck/?p=5302 Three interesting case studies this week in the use of social media in my journalism (or in one case just my life), which I hope might be of some interest to others (especially colleagues who have been skeptical of its utility – you know who you are). 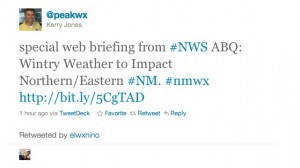 New Mexico had a historic storm this week, a freeway-clogging, school-closing, pipe-freezing, gas-service-interrupting mess. One of my jobs at the newspaper is to pay attention to the weather and explain/warn as needed. I could not have done that, or done it as well, without Twitter. New Mexico had a historic storm this week, a freeway-clogging, school-closing, pipe-freezing, gas-service-interrupting mess. One of my jobs at the newspaper is to pay attention to the weather and explain/warn as needed. I could not have done that, or done it as well, without Twitter.
Every newsroom I’ve worked in over the decades has had, as its soundtrack, the chatter of a police scanner. We know how to use that – quick bursts of information, often unconfirmed, that are worth paying attention to in a low level, background way. My Twitter feed is like that, but on a broad range of topics. It includes, for example, a number of people working at the National Weather Service’s Albuquerque office, who do a great job of sending out links to their latest forecast information, interesting data, and a heads up when the weather is about to get interesting. (That’s Kerry Jones and Daniel Porter you see in the accompanying picture, passing along a link to Daniel’s latest storm update.) My feed also includes other journalists, emergency services folks (both agency and individual feeds) and a lot of regular people who live around New Mexico. When an event like our epic cold happens, the chatter picks up, creating an ambient awareness of the developing situation – tidbits to check out, alerts from government officials, journalists linking to their latest info, people asking questions, other people giving answers. There is, for example, Melwell Romancito up in Taos, where the gas has been off for more than 48 hours. I have no idea who she is, but people started Retweeting her stuff, I followed her, and she’s become a great source of information. (She just pointed out a problem with some info that’s currently making the rounds from an earlier gas company release. Turns out we still have that info on the newspaper’s web site. Must get it fixed.) Or TaosJohn, who shared a link to the Taos Police Department Facebook page. There also are official channels, like the New Mexico public safety folks. This is the sort of ongoing, rapid fire communication that has always gone on in a story like this – trying to reach out and communicate as quickly as possible with a range of people who might have relevant information. Twitter is simply a huge force multiplier. The second case study is far simpler and less freighted, but has a lot of similarities. I don’t write much directly about economics, but it is an important boundary condition for a lot of what I cover – water policy, energy, environmental issues. So I try to have a sort of ongoing ambient awareness about what’s going on in the economy, to help me understand when I need to dive into in more detail. My Twitter feed includes a list of economists and economics journalists (and probably some people who are both) that acts as a sort of police scanner for the economy. When Friday’s confusing set of jobs/unemployment numbers came out, I didn’t have the time or the expertise to sort it out myself. But that was OK, because the people I follow on Twitter did it for me in a 24-hour burst of shared links – first alerting me to the data release, then taking me through the sorting out they were all doing. Again, this is the sort of thing I could have done (and often still do) in other ways – hunting through the econ blogs and work of various journalists or diving into the data myself. Twitter made it far easier and more serendipitous. There are a lot of other subject areas like these – New Mexico politics and the state legislature, climate science and politics, energy policy, western water – where a carefully assembled Twitter feed of smart people chatting about what they know is an incredibly useful way of tracking what’s going on. Having the equivalent of a police scanner for the water policy beat is awesome. In the previous cases, I am my own “curator”, picking which feeds to follow, getting a feel for who to listen to and how. The previous cases also relate directly to my job. The final case study is Egypt, where I’ve joined 39,414 other twitter users (as of 8:27 p.m. MST Saturday) and outsourced the curation to Andy Carvin. Amy Gahran at Knight Digital Media explains a bit about who Carvin is (NPR “senior strategist”, whatever that means) and how he’s doing it. The bottom line is that he’s find and sharing information at an amazingly rapid fire and amazingly useful rate. Plus, there’s ro_bot_dylan. Related posts: - Social Media Signposts
- On Media and Bunk
- A Problem the News Media Can’t Fix
- Harlow the Journalist
- RSS
Related posts brought to you by Yet Another Related Posts Plugin.
I have my Twitter info page here: http://www.joe-anybody.com/id143.html ~joe anybody
Posted by Joe Anybody
at 8:46 PM PST
Thursday, 3 February 2011
Mubarak intensifies press attacks with assaults, detentions
Mood:
 don't ask
Now Playing: protesters in Egypt ATTACKED
Topic: HUMANITY don't ask
Now Playing: protesters in Egypt ATTACKED
Topic: HUMANITY
 SIPA Press agency photojournalist Alfred Yaghobzadeh is treated by anti-government protesters after being wounded during clashes in Cairo. (AP) http://cpj.org/2011/02/mubarak-intensifies-press-attacks-with-assaults-de.php New York, February 3, 2011--Egyptian President Hosni Mubarak unleashed an unprecedented and systematic attack on international media today as his supporters assaulted reporters in the streets while security forces began obstructing and detaining journalists covering the unrest that threatens to topple his government. "This is a dark day for Egypt and a dark day for journalism," said CPJ Executive Director Joel Simon. "The systematic and sustained attacks documented by CPJ leave no doubt that a government-orchestrated effort to target the media and suppress the news is well under way. With this turn of events, Egypt is seeking to create an information vacuum that puts it in the company of the world's worst oppressors, countries such as Burma, Iran, and Cuba. "We hold President Mubarak personally responsible for this unprecedented action," said Simon, "and call on the Egyptian government to reverse course immediately." Here is a round-up of attacks on the press: - The Washington Post told CPJ that they have heard from multiple witnesses that the paper's Cairo bureau chief, Leila Fadel, and Linda Davidson, a photographer, were among a number of journalists detained this morning. Their status was unclear late today.
- The New York Times reported today that two of its reporters were released after they were detained overnight in Cairo.
- Canadian Globe and Mail journalist Sonia Verma tweeted that she was being taken "into some kind of custody." She later reported that she was held by the military for three hours.
- CNN-IBN reported that video journalist Rajesh Bharadwajm was "taken away" from Tahrir Square by military forces. Bharadwajm's status was not immediately clear.
- Government officials, pro-government journalists, and commentators loyal to Mubarak have for the past two days been engaged in a systematic campaign to present foreigners, and particularly foreign journalists, as spies. CPJ has documented at least seven instances on state-owned television or on private stations owned by businessmen loyal to Mubarak in which individuals described elaborate foreign plots to destabilize Egypt that centered on foreign provocateurs, including journalists. In several instances, they were described as "Israeli spies." In one instance, a woman whose face was obscured "confessed" to having been trained by "Americans and Israelis." She went on to say that the alleged training took place in Qatar, where Al-Jazeera is based.
- Mubarak supporters stormed Cairo's Hilton Hotel searching for journalists, Al-Jazeera reported today. Journalists inside the hotel posted a Tumblr entry that said: "About 20 foreign journalists are currently holed up." No injuries were immediately reported, but the journalists' status was unclear.
- Dima Salem, a reporter for Dubai-based Al-Arabiya television, was attacked by pro-Mubarak supporters who took her cameraman's equipment and tried to beat her. Witnesses helped them escape, Al-Arabiya reported on the air.
- Two Al-Jazeera English journalists were attacked by Mubarak supporters, the Qatar-based satellite station reported on the air. Three other network reporters were detained in Cairo, the station reported. No names were given.
- A BBC producer tweeted that Margaret Evans, a CBC reporter, was forced to hand over recording equipment to military forces in Tahrir Square.
- At least four Spanish journalists were attacked in Cairo, according to news reports. Joan Roura, a correspondent for TV3, a Catalan public television station, was attacked by men who tried to steal his mobile phone while he was conducting a live broadcast for the 24 hours news channel. Assaults were also reported against Sal Emergui, a correspondent for Catalan radio RAC1; Gemma Saura, a correspondent for the newspaper La Vanguardia; and Mikel Ayestaran, a correspondent for the newspaper Vocento/ABC.
- Several Turkish journalists were attacked by Mubarak supporters, according to news reports. Cumali Önal of Cihan News Agency and Doğan Ertuğrul of the Turkish Star Daily were attacked and beaten by pro-Mubarak supporters on Wednesday. Both were in stable condition today.
- Men with knives seized Erol Candabakoğlu, a Turkish Fox TV reporter, along with his unidentified cameraman and driver on Wednesday while they were filming in the Boulaq neighborhood of Cairo, according to news reports. The Turkish news agency Anatolia reported that Egyptian police later freed them.
- Metin Turan, a reporter for the Turkish state-run TRT channel, was assaulted today and beaten by Mubarak supporters, who seized his camera, money, and cell phone, according to the Turkish newspaper Today's Zaman. The reporter escaped and sought refuge at the Turkish Embassy; embassy officials told the paper they would take Turan to the hospital because he suffered from wounds and bruises. Isa Simsek, a photographer for Today's Zaman, was also assaulted today by a Mubarak supporter, according to news reports.
- Popular Egyptian blogger Mahmoud (aka "Sandmonkey") tweeted " I was ambushed & beaten by the police, my phone confiscated, my car ripped apar& supplies taken." He said he was briefly detained.
- The British-based communications company Vodafone accused the Egyptian government of hijacking its text messaging services and sending out text messages supportive of Mubarak, according to news reports.
- Multiple journalists for state-owned or government-aligned media have resigned or have refused to work after the government put pressure on them to sanitize the news or to not report on violence against demonstrators, several CPJ sources said. Shahira Amin, an anchor on the state-owned Nile TV channel, said on the air: "I refuse to be a hypocrite. I feel liberated."
Posted by Joe Anybody
at 11:01 AM PST
Monday, 31 January 2011
No Internet - Human RIghts and Social Media Protesters
Mood:
 loud
Now Playing: INTERNET BLACKOUT IN EGYPT DURRING PROTEST
Topic: TECHNOLOGY
http://www.techworld.com.au/article/374871/microsoft_shifts_some_work_egypt/ loud
Now Playing: INTERNET BLACKOUT IN EGYPT DURRING PROTEST
Topic: TECHNOLOGY
http://www.techworld.com.au/article/374871/microsoft_shifts_some_work_egypt/
INTERNET BLACKOUT IN EGYPT
The Think Tank Cafe in the Smart Villages hi-tech park in Cairo. (Image: Smart Villages) WASHINGTON -- Egypt has been aggressively attracting tech companies to its wired office parks to help create jobs for its young, educated and often English-speaking workforce. But by cutting off Internet access last week in the wake of civil unrest, Egypt's government demonstrated just how quickly it can unwind its hi-tech goals.Microsoft is among the 120 companies located in Cairo's Smart Villages , an office park created in 2003 to be Egypt's "prime" information technology park. It includes a health club, swimming pool, video conferencing services, a conference center and a pyramid-shaped restaurant called the "Think Tank Caf." Egypt's move to block Internet access prompted Microsoft to respond. Asked about the situation in Egypt, Microsoft said in a written response to a query that it "is constantly assessing the impact of the unrest and Internet connection issues on our properties and services. What limited service the company as a whole provides to and through the region, mainly call-center service, has been largely distributed to other locations."Another tech firm with a presence in Smart Villages is Hewlett-Packard, which has asked it employees to stay at home . President Barack Obama and other administration officials are urging the Egyptian government to restore Internet services and see access as a human right. "It is our strong belief that inside of the framework of basic individual rights are the rights of those to have access to the Internet and to sites for open communication and social networking," White House Press Secretary Robert Gibbs said at a briefing Friday. Egypt's decision to cut Internet access was apparently intended to disrupt the ability of protestors to use social networks to organize . But hi-tech companies have similar flip-the-switch abilities and can shift services in response to a natural or manmade disaster. It is almost certain that tech companies in Egypt will respond to the current uncertainty much the same way Microsoft did -- if they haven't already. Phil Fersht, the CEO and head of research at Horses for Sources, an outsourcing research and advisory firm, said top-tier providers rely on Egyptian resources largely for call center work and software support and development. For these firms "it's a massive, massive concern when the government shuts off the internet and all hell is breaking loose," he said in an e-mailed response to questions." Egypt has proven capable as a good quality resource location for the Middle East, Africa and European regions in areas such as IT, BPO and call center services and has invested significantly in promoting its capabilities worldwide," said Fersht. "The country has invested millions to promote its capabilities -- and now that investment is looking under threat."Not surprisingly, the government agency responsible for hi-tech development in Egypt, the Information Technology Industry Development Agency, (ITIDA), has been offline. Efforts to reach officials by telephone, e-mail or through a Facebook account have been unsuccessful.Fersht suggested that the current problems in Egypt could prompt hi-tech firms to re-think the risks they face in other regions."If situations, such as what is currently happening in Egypt, proliferate to other countries with sourcing support services, the first reaction of governments now seems to be to 'shut off the Internet,'" said Fersht, "You have to question how this impacts ITO/BPO services that are hugely reliant on the Internet to succeed." The Egypt situation is a serious blow to many of the developing nations seeking to take their share of global services [that] have potentially questionable political stability," said Fersht.Smart Villages said that by the end of 2009 there were 28,000 professionals working at various companies in the office, and that by 2014 it expected that more than 100,000 would be working at some 500 companies.Microsoft is one of numerous tech firms with a presence in Egypt's Smart Villages hi-tech park. Follow Patrick on Twitter at @DCgov or subscribe to Patrick's RSS feed . His e-mail address is pthibodeau@computerworld.com .
Posted by Joe Anybody
at 8:58 AM PST
Updated: Monday, 31 January 2011 9:00 AM PST
Sunday, 30 January 2011
Working Around the Internet Kill Switch - Egypt workarounds
Mood:
 lyrical
Now Playing: Explaining the tech work-arounds for keeping the "net connected"
Topic: TECHNOLOGY lyrical
Now Playing: Explaining the tech work-arounds for keeping the "net connected"
Topic: TECHNOLOGY
Without Internet, Egyptians find new ways to get online Nancy Gohring and Robert McMillan "When countries block, we evolve," an activist with the group We Rebuild wrote in a Twitter message Friday. That's just what many Egyptians have been doing this week, as groups like We Rebuild scramble to keep the country connected to the outside world, turning to landline telephones, fax machines and even ham radio to keep information flowing in and out of the country. Although one Internet service provider -- Noor Group -- remains in operation, Egypt's government abruptly ordered the rest of the country's ISPs to shut down their services just after midnight local time Thursday. Mobile networks have also been turned off in some areas. The blackout appears designed to disrupt organization of the country's growing protest movement, which is calling for the ouster of Egyptian President Hosni Mubarak. "[B]asically, there are three ways of getting information out right now -- get access to the Noor ISP (which has about 8 percent of the market), use a land line to call someone, or use dial-up," Jillian York, a researcher with the Berkman Center for Internet & Society, said via e-mail. Egyptians with dial-up modems get no Internet connection when they call into their local ISP, but calling an international number to reach a modem in another country gives them a connection to the outside world. We Rebuild is looking to expand those dial-up options. It has set up a dial-up phone number in Sweden and is compiling a list of other numbers Egyptians can call. It is distributing information about its activities on a Wiki page. One of the dial-up numbers is run by a small ISP called the French Data Network, which said it was the first time it had set up such a service. Its modem has been providing a connection "every few minutes," said Benjamin Bayart, FDN's president, speaking in an online chat. The international dial-up numbers only work for people with access to a telephone modem and an international calling service, however. So although mobile networks have been suspended in some areas, people have posted instructions about how others can use their mobile phones as dial-up modems. The few Egyptians able to access the Internet through Noor, the one functioning ISP, are taking steps to ensure their online activities are not being logged. Shortly before Internet access was cut off, the Tor Project said it saw a big spike in Egyptian visitors looking to download its Web browsing software, which is designed to let people surf the Web anonymously. "We thought we were under denial-of-service attack," said Andrew Lewman, the project's executive director. The site was getting up to 3,000 requests per second, the vast majority of them from Egypt, he said. "Since then we've seen a quadrupling of Tor clients connecting from Noor over the past 24 hours," he said. Even with no Internet, people have found ways to get messages out on Twitter. On Friday someone had set up a Twitter account where they posted messages that they had received via telephone calls from Egypt. A typical message reads: "Live Phonecall: streets mostly quiet in Dokki, no police in sight. Lots of police trucks seen at Sheraton." Others are using fax machines to get information into Egypt about possible ways to communicate. They are distributing fax machine numbers for universities and embassies and asking people to send faxes to those numbers with instructions about how to use a mobile phone as a dial-up modem. Members of the hacker group Anonymous have also been getting in on the act. They are reportedly faxing some of the latest government cables from WikiLeaks which reveal human rights abuses under President Mubarak, to locations in the country, according to Forbes magazine. We Rebuild describes itself as "a decentralized cluster of net activists who have joined forces to collaborate on issues concerning access to a free Internet without intrusive surveillance." It has set up an IRC for people who can help with ham radio transmissions from Egypt. They are trying to spread the word about the radio band they are monitoring so that people in Egypt know where to transmit. Some ham enthusiasts are setting up an FTP site where people can record what they hear and post the recordings. So far, they say they've picked up Morse code messages. Allen Pitts, a spokesman for the National Association for Amateur Radio, said no one has picked up any voice transmissions from Egypt for the past couple of days. But it's possible that people in Egypt are transmitting over shorter-range frequencies that carry only 30 or 50 miles, he said. One problem with ham radio is that most people who know how to use it in Egypt were probably trained by the military and may be opposed to the protests. Others may be wary of transmitting because they are worried about who might be listening. During earlier protests in Iran and Tunisia, the governments clamped down on specific websites, but access to the Internet was not severed in such a wholescale fashion. It is not unprecedented though. In a blog post Friday written with a colleague, York from the Berkman Center for Internet & Society noted that in 2005 the government of Nepal cut off the Internet connection there, and in 2007 the Burmese government did the same in that country. Nancy Gohring covers mobile phones and cloud computing for The IDG News Service. Follow Nancy on Twitter at @idgnancy. Nancy's e-mail address is Nancy_Gohring@idg.com
Posted by Joe Anybody
at 12:01 AM PST
Newer | Latest | Older
|
| « |
February 2011 |
» |
 |
| S |
M |
T |
W |
T |
F |
S |
|
|
1 |
2 |
3 |
4 |
5 |
| 6 |
7 |
8 |
9 |
10 |
11 |
12 |
| 13 |
14 |
15 |
16 |
17 |
18 |
19 |
| 20 |
21 |
22 |
23 |
24 |
25 |
26 |
| 27 |
28 |
|



 This is what happened in Egypt Jan. 25 prompted by citizen protests, with sources estimating that the Egyptian government cut off approximately 88 percent of the country’s internet access. What do you do without internet? Step 1: Stop crying in the corner. Then start taking steps to reconnect with your network. Here’s a list of things you can do to keep the communication flowing.
This is what happened in Egypt Jan. 25 prompted by citizen protests, with sources estimating that the Egyptian government cut off approximately 88 percent of the country’s internet access. What do you do without internet? Step 1: Stop crying in the corner. Then start taking steps to reconnect with your network. Here’s a list of things you can do to keep the communication flowing. As mass revolt spreads across Egypt and the Middle East and citizens there demand jobs, civil liberties and an end to police state abuses from repressive, U.S.-backed torture regimes, the Obama administration and their congressional allies aim to expand one right here at home.
As mass revolt spreads across Egypt and the Middle East and citizens there demand jobs, civil liberties and an end to police state abuses from repressive, U.S.-backed torture regimes, the Obama administration and their congressional allies aim to expand one right here at home.


